A very real threat
In the last two years, ransomware attacks have targeted companies, governments, municipalities, health care, the financial services and insurance sectors, and many others. They have become common events. Their scope is growing and the impacts are extending: substantial reputational damage, lost productivity, legal implications, recovery expenses, and damages to infrastructure and operations.
Many companies are prepared to pay millions of dollars to quickly resume operations. Canadian victims consequently continue to give in to ransom demands because of the high costs and other consequences of refusal to pay, including loss of revenues, the risk of information theft and the cost of network reconstruction.
In the meantime, the coronavirus pandemic has made Canadians even more dependent on cyberspace and digital infrastructure. The quick shift to telework, connected services and Cloud-based applications have added to the weight of various security challenges faced.
Are your business systems and data sufficiently protected?
When a ransomware attack takes place, it is estimated that pirates penetrated your network, on average, about 200 days prior, even before starting to encrypt your data. This precious time often allows them to understand the specifics of your network and to extend their attack to your protective measures such as backups and recovery site.
These attacks are becoming more and more sophisticated and are targeting not only your data, but also your backups! Pirates have understood that these are your main means of recovery and a way to get out of paying a ransom. That’s why backup protection is just as important as protecting your production data. It is in fact the last means of recovery in case of data encryption.
Why is the current security approach lacking?
- User workstations are rarely equipped with effective, up-to-date and complete protection solutions.
- Basic security functions (e.g. Windows security) are often deactivated.
- Remote business network access (e.g. VPN connections, RDP) presents significant vulnerabilities if they are not corrected.
- Organizations rarely put in place effective security monitoring and intrusion detection services.
- Data stored on servers and file systems is rarely encrypted.
- Network-connected backup infrastructure is itself becoming a priority target for pirates.
- Data replication to a second site (e.g. backup site) risks extending and accelerating the spread of the attack if unprotected.
- The data recovery process using tapes can take weeks while financial losses due to an attack continue to accumulate each day.
- There are often no detection mechanisms for changes to your IT environments.
- Cyber-insurance plans are highly complex and only cover a small fraction of potential losses.
Pressing need to review current approaches. Necessity of innovative, next generation solutions.
Implementing a protection strategy against ransomware attacks requires a 360-degree review of your environment and practices. This is exactly the type of service Converge’s specialized cybersecurity group can offer. The aspect we want to focus on today, however, is backup and recovery mechanisms, which are the last means of protecting your data from pirates.
Because of the complexity and increasing level of sophistication of attacks, we often consider data protection the most urgent element to update, especially if clients doubt the effectiveness of their current backups.
In general, organizations use a multi-layer or multi-tier approach, which is very good in theory. The challenge is that, too often, backups have become neglected within their infrastructure and have not been updated for many years, making them a priority target for pirates. At the same time, several changes have taken place and transformed the company’s data management.
VMware Cloud Foundation helps you automate infrastructure and operations management, and reinforce security on both private and public Clouds.
Here are a few examples:
- Data protection for teleworking employees
- Security of sensitive data stored on the Cloud
- New hybrid, multi-Cloud and multi-site realities
- Application modernization initiatives
- Development projects in DevOps and Agile mode
- Container technology integration (Kubernetes)
- Adaptation to new Cloud platforms and native services
Next-generation data protection platforms such as Cohesity, PureStorage, or Cloud services (IaaS) are introducing a series of innovations to your environment. One of the main ones is software-defined management, which enables, simplifies and automates data protection.
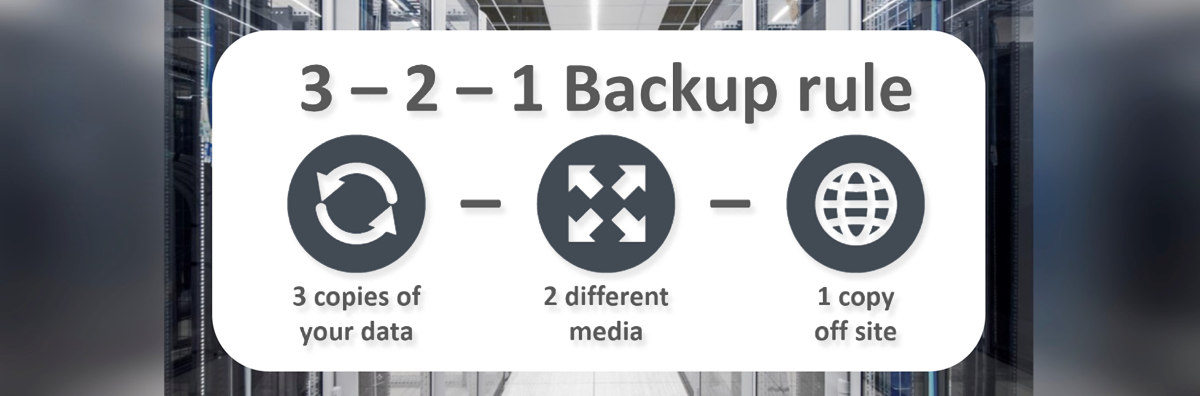
Principles of the 3-2-1 rule
The 3-2-1 rule is often cited as an enterprise best practice in data protection and storage.
- Always keep three (3) copies of enterprise data.
- Maintain two (2) copies of data on-premise, on two different medias: a primary storage unit (e.g. disk system) and a specialized unit. (e.g. back-up appliance).
- Store one (1) copy of replicated data offsite on another unit such as a specialized back-up appliance, a tape library or on the Public Cloud.
- The choice of solution architecture and the mix of medias and technologies will vary based on the company’s RPOs, RTOs and other business obligations.
The advantage of software-defined management is that data can be qualified and structured based on enterprise policies. These rules and corporate policies are then embedded in the software and applied to data according to its value, level of importance, enterprise retention practices and legal obligations, level of performance, availability or security required. Software intelligence is then used to adapt these protection strategies, to automate data transfers or to isolate data on your infrastructure or the Cloud. This is how we build Cyber-Recovery Vault solutions to fight against Ransomware attacks.
Other advantages:
- Protect backup data with a reliable operating system.
- Take advantage of several backup copies for analysis and detection of possible anomalies.
- Perform analyses without using production data infrastructure, which often offers a very limited range.
- Establish a set of automated anomaly identification processes if abnormal behaviours or changes are observed on your IT environment
To read Part 2 of this article on Ransomware Attacks – Cyber-recovery vault principles: Click here
Next step
No matter at what stage your team finds itself, the members of our professional services group can help, starting with asking the right questions and guiding you one step at a time toward a protection strategy adapted to your organization.
Questions
Feel free to send us your questions or comments. We look forward to discussing possible solutions with you.
To better understand our services and how PCD can help, visit the Data Protection section on our website.
Jimmy Grondin
Solution Architect, Storage and Data Protection
PCD Solutions, a Converge company
jgrondin@pcdsolutions.com