When we look at the number of organizations that have been forced to pay a ransom, it’s clear that current defences are inadequate. It is estimated that, on average, hackers have penetrated your network for about 200 days before triggering data to be encrypted. A precious time that often allowed them to understand the ramifications of your network and above all, to attack your protective measures such as backups and disaster recovery site.
The traditional approach is lacking on several fronts:
- User workstations are rarely equipped with effective, up-to-date and complete protection solutions.
- Basic workstation protection functions (e.g. Windows) are often deactivated by default.
- Remote business network access (e.g. VPN, RDP, etc.) presents significant vulnerabilities that are often not corrected.
- Organizations rarely put in place connected services for security monitoring and preventive intrusion detection.
- Data stored on servers and file systems is rarely encrypted.
- Network-connected backup infrastructure becomes itself a priority target for pirates.
- Data replication to a second site (e.g. backup site) only accelerates the spread of the problem.
- Recovery processes using tapes can take weeks while financial losses due to a ransomware attack continue to accumulate each day.
- Cyber-insurance plans are highly complex and only cover a small fraction of potential losses.
The urgency of putting in place new ways of doing things
First, we need to pause to better understand how these attacks take shape and spread. Knowing that attacks are constantly evolving, it is necessary to take a global and dynamic protection approach. We must increase employee awareness and training, and regularly review at-risk practices that often lead to spreading attacks to other colleagues or the network through a lack of preparedness to manage such an incident.
From a technological perspective, some security innovations are very helpful in detecting, isolating and automating defence mechanisms to limit the scope of attacks. They also speed up system and data recovery.
Here is an excellent example:
In terms of data protection, organizations generally use a multi-layer or multi-tier strategy. Business data is categorized based on its value, level of importance (RTO / RPO), age, cost, company policies, and level of performance, availability or security required. Software policies and technologies are then used to facilitate movement of data to different infrastructure layers, namely:
- Primary storage
- Secondary storage
- Tape protection
- Cloud
Two of these layers are used at a minimum. The primary and secondary storage layers often reside on-premise in the company’s datacentre. This data stored on Flash technologies or disks ensures effective access and quick recovery when needed.
With the quantity of data exploding and becoming increasingly difficult to manage, many companies have taken advantage of secondary storage units. These are equipped with compression and deduplication technologies to store a maximum of data while using less storage space. Nevertheless, the expansion thresholds observed are forcing IT teams to regularly free up these specialized units by sending data to a longer-term storage media. To that end, some businesses use libraries and tape systems while others now actively use the Cloud.
The challenge is therefore to appropriately expand data security management to each of these layers using a simple, consistent and integrated approach. It must also be done while meeting business groups’ expectations as to targeted levels of service (SLA), recovery point objectives (RPO) and recovery time objectives (RTO).
The 3-2-1 rule
Many companies follow the 3-2-1 rule, which consists of:
- always keeping three (3) copies of data;
- maintaining two (2) copies of data on-premise, on two different medias: a primary storage unit (e.g. Dell EMC PowerMax, PowerStore, PowerScale (NAS) disk systems or HCI Dell VxRail+vSAN solution) and a specialized deduplication unit (e.g. Dell EMC PowerProtect);
- storing one (1) copy of data replicated offsite on another unit such as an appliance (e.g. Dell PowerProtect), a tape library or the Cloud (e.g. Azure, AWS), based on targeted RPOs and RTOs.
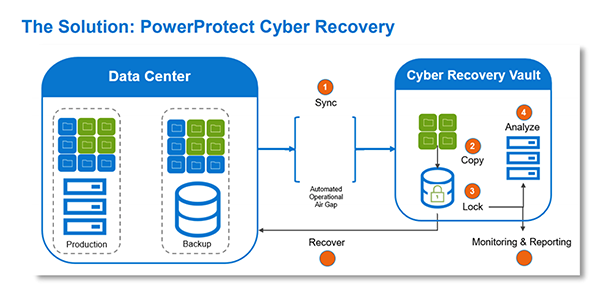
Dell EMC PowerProtect / Cyber Recovery Solution
Cyber-recovery vault principles
Unlike backup infrastructure or a complete backup site, the Dell EMC Power Protect Cyber Recovery vault is a solution specifically focused on protecting essential data and its recovery in case of cyber-attack.
- The most business-critical data sets and system configuration data are identified in advance.
- This critical data is isolated in an electronic vault outside of the rest of the network, with no external IP link to the vault.
- Automated software policies are used to encrypt and synchronize data once a day through replication, breaking the link between each sequence (air gap).
- The backup software target manages replication as well as a continuous security and integrity analysis of idle data.
- The data stored externally in the vault is encrypted and managed through distinct access accounts for authorized officers designated by the company.
- Golden image copies are also kept for main business systems and executable source codes of applications considered the most critical in order to speed up recovery.
The different principles applied when creating a cyber-recovery vault stem from the Sheltered Harbor approach, which is made up of a set of proven and modern security rules and practices that aim to ensure confidence in the integrity of financial systems in the US and around the world. The cyber-recovery vault solutions deployed in Canada by our governments and many private institutions and businesses draw their inspiration from this approach.
Link to Dell EMC Cyber Recovery – Interractive Brochure
Countering attacks with the Dell Cyber Recovery solution
Dell aims to help businesses minimize their risks by proposing a simple and integrated end-to-end solution. The Dell EMC Power Protect Cyber Recovery solution integrates with your business architecture as a secondary storage technology. It is positioned between your primary storage systems and the integrations with your duplication software, tape library systems (if applicable) or Cloud provider services such as AWS or Azure for long-term data retention.
Proven, modern and intelligent, Dell’s PowerProtect Cyber Recovery solution is agnostic from your primary storage infrastructure vendor and/or back-up software solution. It automates workflows to protect and isolate strategic data. It also identifies suspicious activities and accelerates data recovery to help you quickly resume normal operations. Here are the solution’s key functionalities:
- Automated workflows following predefined rules to safely move strategic data to the isolated vault.
- Data deduplication ratios up to 72:1.
- An intuitive and powerful dashboard that gives you the possibility of creating protection rules in fewer than five steps.
- Automated data isolation for mission-critical systems based on your own data governance rules.
- CyberSense analytics that provides real-time monitoring and tracking of potential data integrity threats.
- Powerful analysis and detection tools to diagnose and correct weaknesses in continuous mode.
- Necessary integrations with many third-party tools and software involved in data protection for various platforms.
The Dell PowerProtect Cyber Recovery solution allows data to be stored and encrypted by an intelligent algorithm, thus making it immune to any form of ransomware attack. The Dell Cyber Recovery technology is used in various architecture scenarios with one, two or several ROBO sites to implement cyber-recovery vault principles and ensure an optimal level of protection. Variants include local mode solutions or beneficial Cloud scenarios.
Introduction video – Dell EMC Cyber Recovery solution
Best practices for protection against ransomware attacks
Naturally, the above information on data protection and cyber-recovery vaults is but one aspect of the fight against ransomware attacks. Many other elements come into play and are just as important to consider.
Here are a few such elements:
- Ensure the systematic and automatic application of available software patches for known vulnerabilities within client workstations, the network and server environments.6
- Make sure that client workstations are effectively protected against ransomware and other malware (e.g. VMware CarbonBlack protection suite).
- Evaluate the possibility of virtualizing workstations to centralize data management and workstation security control from your datacentre (e.g. VDI VMware Horizon solution).
- Implement an intelligent enterprise firewall solution with managed intrusion detection services (e.g. Palo Alto Networks).
- Regularly review possible security weaknesses with members of your internal IT team.
- Take a network segmentation (microsegmentation) and subnetwork isolation approach to limit the scope of an attack6 (e.g. VMware NSX-T).
- Make sure to address vulnerabilities such as Zerologon that can accelerate an Active Directory domain takeover if patches are not applied.6
- Review your Active Directory infrastructure to ensure it is well protected and robustly designed, in distinct tiers based on role criticality.6
- Ensure that data backups are performed daily, ideally according to the 3-2-1 rule.
- Make sure that a copy of this data is encrypted and stored in an external cyber-recovery vault disconnected from the business network.
- Regularly perform system and data recovery process test exercises (at least four times a year).6
- Continue to advance and update your security practices based on trend analyses and the evolving nature of attacks.6
Source 6: CISA – https://www.cisa.gov/publication/ransomware-guide
Next step
No matter at what stage your team finds itself, the members of our professional services group can help, starting with asking the right questions and guiding you one step at a time. We can provide advice and support you in quickly implementing a protection strategy adapted to your organization.
Questions
Feel free to send us your questions or comments. Contact us. (info@pcdsolutions.com)
We look forward to discussing possible protection solutions with you.
Jimmy Grondin
Solution Architect, Data Protection
PCD Solutions, A Converge Company