In the last six months alone, more than 715 vulnerabilities were discovered within remote access systems, VPN connections and online RDP services, often lacking network layer authentication (NLA). The increased use of Web applications to connect to certain critical business systems is also a contributor.
Cybercrime has been on the rise in terms of the number of incidents, their importance, their level of sophistication and their financial impact. Just like their techniques, the actors behind these attacks continue to evolve very quickly.
Businesses and public organizations in Quebec are confronted with new forms of cyberattacks now more than ever
Here are some facts:
- It is estimated that an attack now takes place every 39 seconds in North America, representing 2,244 attacks each day.1
- 92% of the organizations surveyed admit to not having adequate mechanisms in place for detecting these threats.1
- In 88% of intrusions, it has been shown that in less than 12 hours, a pirate succeeded in penetrating the network, taking control of different systems and extracting targeted data.3
- 71% of attacks recorded in North America are motivated by financial extortion.4
- While the majority of attacks target large companies, 43% affected small and medium-sized enterprises in 2020.4
- The number of ransomware attacks recorded by Canadian businesses and public organizations in 2020 increased by 4,000%.5
- Nearly 70% of these businesses were unprepared and therefore forced to pay a ransom to regain access to their data.5
Source 1: USA Security Magazine
Source 2: Verizon 2019 Security study
Source 3: CRN
Source 4: Accenture 2019
Source 5: Canada’s National Observer
What is a ransomware attack?
Generally speaking, the ransomware cyberattacks that target organizations’ data are RansomLockers and CryptoLockers. This type of malware is also called a cryptovirus or Trojan horse. They are often transmitted through email attachments, infected programs or websites, or direct network intrusions. They normally infect a workstation and then attempt to access the company’s network and extend the scope of the attack.
Pirates often use a keylogger to gain administrator access in order to penetrate the network, then take charge of domain controllers, server environments and file services. They then launch an attack using encryption technologies to prevent access to your data, documents and files, making them unusable without the decrypting key. Today, these attacks even go so far as to compromise the integrity of your backup systems and infrastructure, since pirates understand that these are your only options for recovery.
The spread of ransomware attacks is not to be taken lightly. They have the potential to paralyze all of your company’s operations, including emails between employees, clients and business partners.
Pirates usually demand a ransom, that can quickly reach several thousand dollars, to allow you to regain access to your data. Recent attacks have even been using double extortion: one ransom payment to decrypt data and another to avoid the disclosure of sensitive data, which could harm your company’s reputation.
Unfortunately, there are currently no tools or technologies powerful enough to unblock access to encrypted data. Ransomware attacks have therefore become quite lucrative; they have multiplied and are now controlled by various organized crime figures.
If you believe your company to be immune to attacks because you use Mac computers, Linux workstations rather than Windows, or tablets and smart phones, be aware that cryptoviruses can attack all kinds of devices.
Should we agree to pay a ransom?
The scope and impact of a ransomware attack vary based on each organization’s profile. We can, however, agree on the basics of enterprise risk and cost assessment exercises.
It is interesting to note that even though the practice recommended by authorities and experts in the security field is never to pay a ransom, 70% of organizations have done it, seeing themselves as having no other options once an attack has been launched. It should also be noted that at the slightest intention to pay, a process of negotiation begins between the parties, which can double or even quintuple the amount. Paying the ransom is also a guarantee that other attack attempts will follow on an ongoing basis. It is therefore necessary to quickly put in place permanent and effective protection measures.
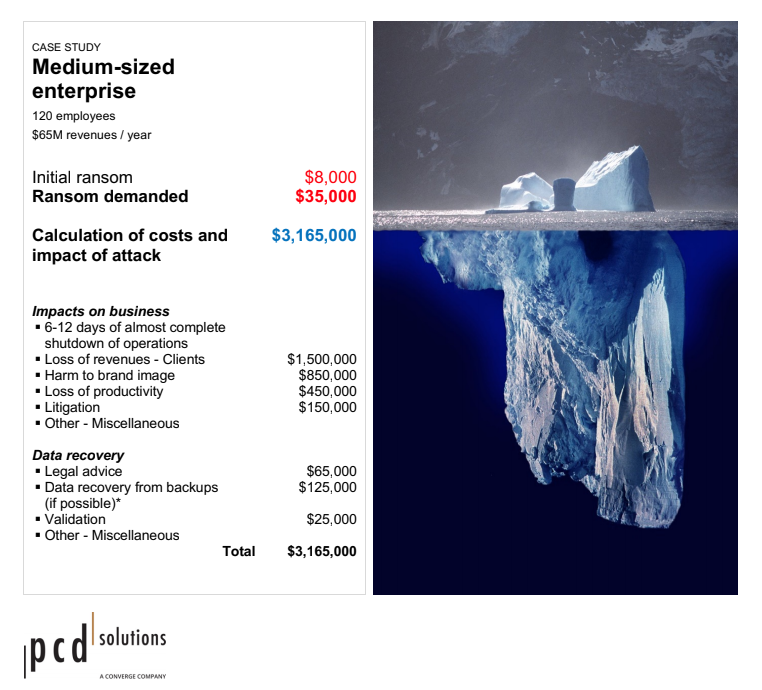
Here is an example of a medium-sized enterprise:
What is the role of authorities vs that of businesses in all this?
Although the government is working to educate businesses about putting defences in place, many would say that guidelines remain vague. In Quebec, Bill P-64 tabled by the Quebec government is somewhat controversial, but remains a precursor for establishing a set of recommendations and obligations for businesses and public organizations to protect citizens’ personal data. It will increase pressure to implement preventive security measures.
With all the money and efforts invested in the government’s digital shift, just as in the private sector, we can expect new standards and regulations in Canada in the near future. Until then, many companies have already begun implementing different solutions inspired by cyber resilience principles, either in the US or Europe (FFIEC, GDPR, HHS HIPAA Guidance, Sheltered Harbor, FBI Cyber Defense Best Practices).
In any case, the ultimate responsibility for protecting data remains that of organizations. There is still a lot of confusion about recommended defences. Before focusing on a solution based on select defences or technologies, you must first and foremost establish your organization’s needs, obligations and protection strategy.
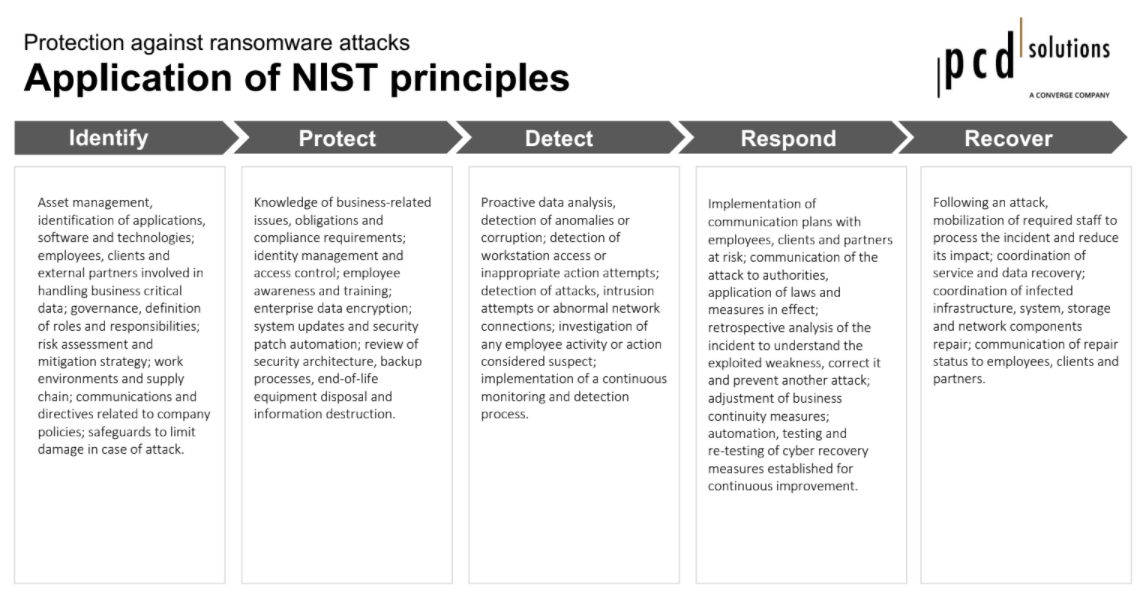
Here is an example of a ransomware attack protection plan exercise according to NIST principles:
This internal reflection will then allow us to guide the organization toward a solution that is realistic, pragmatic and adapted. As a provider for this type of project, we ourselves have had to define our response capabilities and finalize our approach by working with our partners, namely within the Converge family, who complement our expertise.
In our own areas of expertise, including IT infrastructure, datacentres, data protection solutions and more recently the Cloud, we find that traditional backup and recovery approaches are tools but are no longer enough to ensure protection against attacks. The next-generation solutions proposed now include a range of services aimed at raising user awareness, installing advanced detection technologies on workstations, systems and networks, and creating cyber recovery vaults that are entirely disconnected (air-gap) from the network. We also use network virtualization and microsegmentation principles to support the deployment of a distributed protection (software-defined management) to isolate systems and limit the scope of potential attacks. These topics will be covered in future articles:
Cyber recovery vaults
HPE StoreOnce® solution approach
PureStorage & Cohesity FlashRecover® solution approach
Dell EMC CyberRecovery Vault® solution approach
Network isolation and microsegmentation
VMware NSX-T and microsegmentation
Questions
Feel free to send us your questions or comments. Contact us. (info@pcdsolutions.com)
Olivier Ménard, PMP®
Director of Operations, Consulting Services
PCD Solutions, A Converge Company