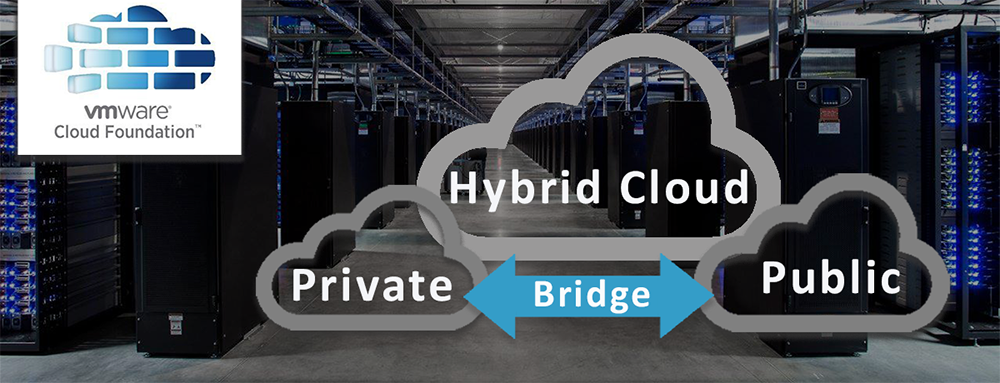
Minimizing attack surface – Keep potential intruders from causing further damage with the right tool…

As encryption-based cyberattacks continue to evolve, it is imperative that organisations proactively seek to better protect themselves. It is no longer enough to simply fortify perimeter security—organisations must find ways to protect themselves from the inside as well. The need for better defence, even after an attacker successfully intrudes, can no longer be ignored. Businesses must act now to avoid potentially devastating consequences.